Spring is upon us… it makes sense that the Spring Framework would have a critical bug right around now, eh?
One of the most difficult things that many organizations faced with Log4Shell was finding instances of Log4J in their environment that they needed to be concerned about. I’m not talking that organizations had developers that didn’t know if they were using Log4J, organizations have Java applications and often may not know the frameworks and libraries being used in each and every application they run; yet they still needed to be able to protect themselves as patches from vendors were pouring in.
It would seem that even though Spring4Shell isn’t getting as much publicity, it is just as (if not more) important to be searching for this vulnerability in our environments. That’s why I launched “Spring Searcher” today. I had a head-start, a lot of the same tools I built for searching for Log4J can be used for searching for Spring Framework without much modification. The hardest part was making the dashboard accessible for mass consumption since I had previously just been spinning up individual instances of the dashboard for my clients when I was looking for Log4J.
My hope is that as these types of vulnerabilities become more and more prevalent that I can simply make a few lines of code different going forward and continue to spin up new versions of this platform as more of these issues come up in the future… but for now, enjoy. You can sign up for free at https://springsearcher.infosecchicago.com/
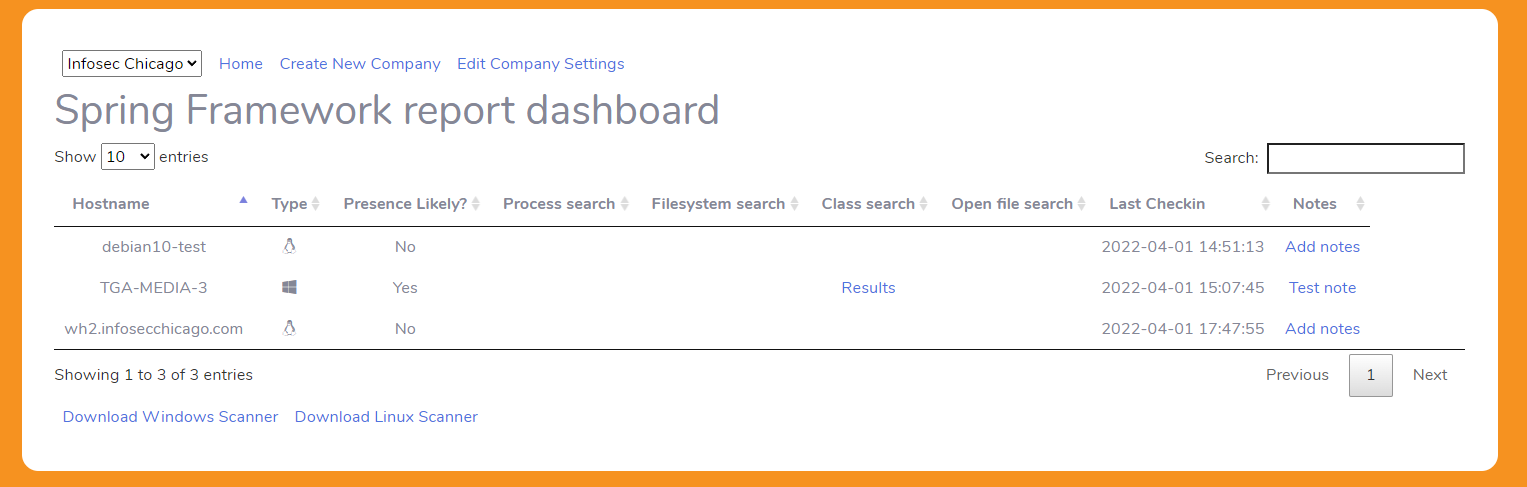
These powershell and bash scripts will search through running processes, files on the system, Java classes in .jar and .war files, and open files for any presence of something that could be springframework and report back to the central dashboard. You can simply download the scripts, pop them into an RMM or other tool and keep hitting F5 until you have the results you need. As you start to remediate, you can keep notes in the platform as well. You can invite multiple users to your platform, and run multiple companies – which makes it great for companies with multiple divisions or for MSPs.
Currently scripts are available for Windows and Linux (tested on Debian 11 and Windows 10). I have a starter script for Mac, but it was a pain when I used it for Log4J, so it will require a bit more work to get that going. If it’s something you would find useful, leave a comment below to help me estimate interest.
The scripts are not persistent, meaning if you want to continue updating the results of each machine, you will need to configure your RMM or other tool to continue running them; but I would suggest running them once, then simply running one more time after that to verify remediation if needed so you don’t have something constantly running on your computers.
The platform is very much in a beta stage, so let me know if you run into problems with it. Since this is a free tool, it’s provided without warranty or guarantee.
