Why should I use ScamBlock at my company?
Tech support scams have been around for quite awhile now, and they seem to be getting more aggressive than ever. Ask almost any security technician what the best defense against these scams is, and they will almost always respond with “training”. While training your users is a huge part of cyber security, it isn’t 100% effective when it comes to keeping your users safe. Let’s face it… as people working in IT, we can see scams a mile away; but to users, those “scare” pages and phone calls can be pretty convincing. That’s where Just In Time (JIT) training comes in. By alerting users about threats while they are happening, they are more likely to be aware that they are being scammed. ScamBlock was invented to do just that (by alerting users when a suspicious program is opening). In addition; by adding a password on the notification window, you can also block some destructive behaviors that the scammer might use. (Such as using syskey to lock the computer.)
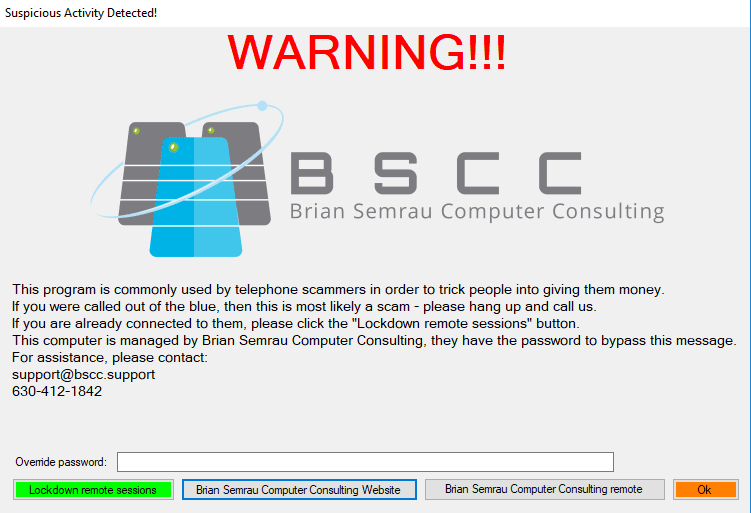
Window shown when syskey attempts to start
What can ScamBlock protect?
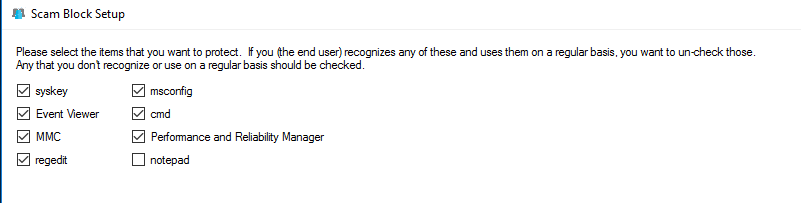
ScamBlock can protect any of the following:
- syskey
- Event Viewer
- MMC
- Regedit
- msconfig
- cmd
- Performance and Reliability Manager
- Notepad
Installing ScamBlock
Start by downloading the executable. You could compile it yourself if you want to run a code review first – the source code is on GitHub. If you prefer to use a pre-compiled executable; simply download it from my website: https://downloads.semrauconsulting.com/SB/SBSetup.exe. For your first install, you will need to go through each of the steps in the GUI.
Launch the executable as an administrator and accept the license agreement.
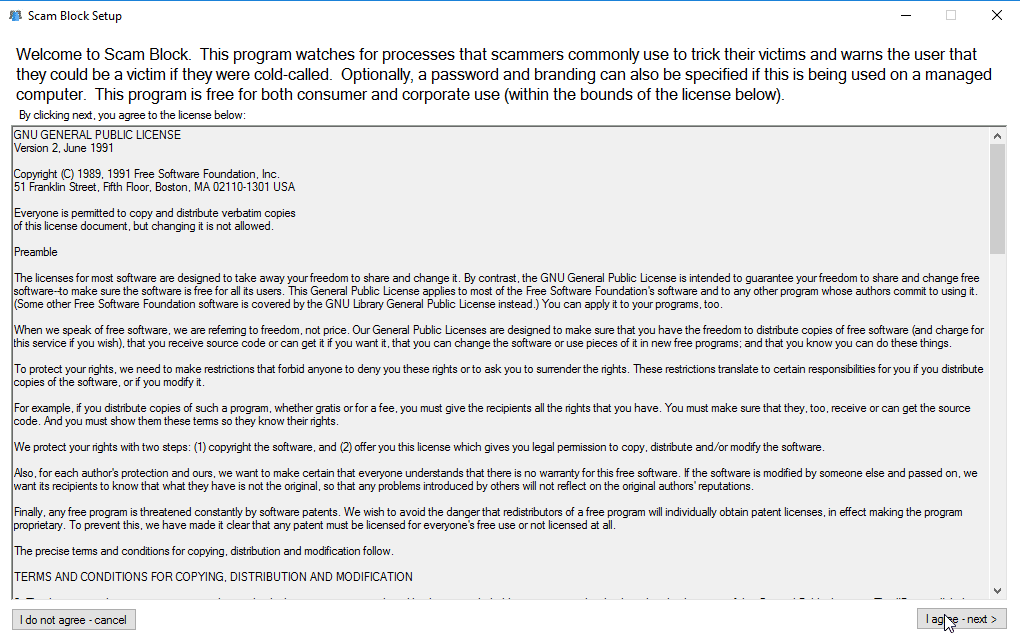
Select “Business/MSP (branded)” and click next.
Enter your branding information, select your logo (a png with transparent background is best), then click next. If you don’t want the user to be able to lockout remote access tools, un-check the box that says “Enable remote connection lockout”. Once you are done, click next.

Select the executables that you would like protected with ScamBlock, then click next.
Confirm the installation directory, then click Install.
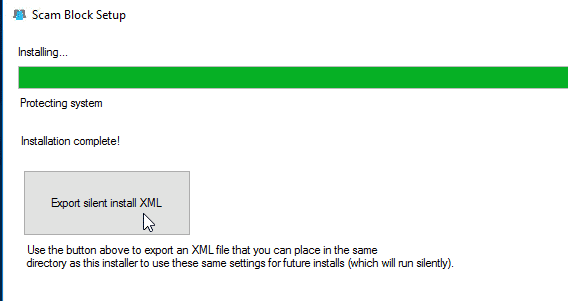
The installer will take about 1 minute depending on the computer and network speeds. Once the installer is done, you can choose to export a XML file with the settings from this installation. The next time you run the installer, if your XML file (and logo if you selected one) is in the same folder as the setup file, the installer will silently use the same settings again.
Once it is installed, give it a shot and open one of the protected executables. You should see the notification popup.
Using ScamBlock
Using ScamBlock is very simple. For the most part, it is “set it and forget it”. It doesn’t sit there running in the background using resources, rather it only runs when someone tries to start a protected executable. As soon as someone runs one of the protected executables, ScamBlock shows a notification window with the information that you configured during setup. This notification window can be easily bypassed (optionally requiring a password that is set during setup). Another useful feature is the remote support lockout function. Should the user already be connected to a scammer, they can click this button to force the scammer to disconnect until you are able to assist them. If the program does not have a definition for the remote access program that the scammer is using, the user can also choose to temporarily disable all network connections on their computer.
FAQ
- Will this replace my AntiVirus/AntiMalware?
- No – absolutely not. This simply shows an alert if you run a system executable that the average end-user would never use.
- Is it really free?
- Yes – for both consumer and enterprise use. It’s also open source (GNU GPLv2), so you can also view/edit the source code on GitHub.
- What systems has it been tested on?
- Windows 10 and Windows 7.
- What are the requirements?
- Local admin rights
- .NET 3.5 or higher
- Active internet connection during installation (to download the necessary components)
- Will this interfere with my RMM or other tools?
- Possibly – I would suggest playing around with it in a VM first. If you don’t protect cmd, you will probably be fine.
- Interaction with various RMM and other automation tools is something I want to test more – especially if cmd is protected. If you are interested in helping with this testing, please leave a comment below – I would love the help.
- Is there any warranty if something goes wrong?
- Nope. I’m not making money off of this and I’m a poor college student.
- I’d like to help… what can I do?
- I would welcome any contributions to the code on GitHub that you might have.
- I would also love any donations that could go towards my school and research expenses. See my donations page for more details. (For enterprise use, just think of how much you would be paying for this if it was a commercial tool!)
- I need to uninstall ScamBlock. How do I do that?
- Use the uninstall batch file here: https://raw.githubusercontent.com/thegeekkid/SuspiciousActBlocker/master/uninstall.bat
- Note, if you protected cmd, you will still get the block notification before you can proceed with the uninstall.
Not a one-stop-fix
Keep in mind that ScamBlock is not a guaranteed solution. Scammers could adapt and use other tools to take advantage of their victims; or even figure out ways around ScamBlock. (I can certainly think of a few ways around it – they would require some effort though.) At the end of the day, active end user training is still highly recommended. ScamBlock is meant to be the last resort security measure. While each security measure that you use can help harden your systems, stopping the attack from ever hitting your defenses is always the best option.
I am in your Facebook group and seen the post with this tool. I had installed it to mess with it but when I went to remove it, I get this error when trying to open device manager now.
Error getting install_type setting. Please send this to support:
System.NullReferenceException: Object reference not set to an instance of an object.
at SuspiciousActBlocker.Form1.get_setting(String name)
Interesting. Did the install complete? For now, try running this “forced” uninstaller: https://downloads.semrauconsulting.com/ScamBlock/ForcedUninstall.exe
If the previous uninstall seemed to have worked correctly other than the device manager issue, it’s worth trying the “normal uninstall” method first, but it probably will not work. If that is the case, try the hash based… that’s pretty robust and should fix the issue.