
Photo credit: wikimedia commons user Duriva (https://commons.wikimedia.org/wiki/File:Socktroll_conspiracy_theorist.jpg)
It seems that almost every week we are hearing about some terrible vulnerability in computing. Unfortunately, many “security” companies use this to scare people into buying their products. One of my pet peeves is “privacy” VPN providers. While some of these companies have good intentions, in most cases they are unnecessary (and in some scenarios can actually cause additional problems).
What is a VPN?
Let’s back up for a second and review what a VPN does. VPN stands for “Virtual Private Network”. To put what it does in a nutshell: it takes your network “packets”, encrypts them, sends them to another network, decrypts them, then sends them to your original destination. This is often used in an enterprise setting to allow employees to access file shares, websites, and other resources remotely that would normally only be accessible from a main office. (Many enterprise VPNs are “split tunnel” though – they will send not “regular” internet traffic across the VPN like a “privacy” VPN would. This helps to keep speeds fast and it reduces resource usage at the “main office”.) There are VPN providers who use this same “corporate” technology to provide “privacy services”. The idea is that if the data is encrypted across an unsecured network (such as a free WiFi network or even your ISP’s infrastructure), prying eyes can only see that you used the VPN, and not what you were browsing. This is (mostly) true; but generally unnecessary.
Why wouldn’t I want a privacy VPN?
Using a privacy VPN sounds like a really good idea at face value; but if you aren’t careful, they can have some serious implications. First of all, they are mostly unnecessary. Most websites these days use SSL/TLS (which encrypts the data exchanged between you and a website). You can check if a website is using SSL/TLS by looking for the “s” in “https”.
![]()
One thing to keep in mind is that a VPN will hide information about what sites you were visiting; whereas SSL/TLS will not. In many cases this isn’t a big deal; but there may occasionally be legitimate reasons to hide the websites that you are visiting. Baring the need to hide that you were visiting certain sites, verifying that your browser is highlighting “https” in green means that it is reasonably secure to log into most websites. (Although, I do argue that there is no such thing as total security.) Another reason not to use a VPN is that it will slow down your browsing speed. Just like it takes longer for you to get to your destination in a car if you have to make a stop that is out of your way first, it takes longer to send your data to another network before it goes to it’s final destination. VPNs are getting better speeds as time goes on; but using one will always result in extra stops that can impact how long it takes to load a website. In addition to being unnecessary and slowing you down, they can actually cause security concerns. To explain that, let’s explore how your data can be compromised on a public network in the first place.
How do crackers extract your passwords from WiFi?
When a password is compromised over a public network, it is almost always due to a “Man in the Middle” (MitM) attack. This is when an attacker tricks your computer into sending all of your data to the attacker before it goes out into the internet. Performing a MitM attack is actually fairly easy; but gaining useful information from that data when a site is using SSL/TLS is difficult and requires additional attacks.
The easiest way to extract data from a MitM attack is to hope that useful data is sent to a page that doesn’t use SSL/TLS. This involves a lot of chance, and pages that do not support SSL/TLS are becoming rare.
The next option would be to run an attack called an SSL strip. This attack tries to tell your browser that the site cannot use SSL/TLS; so in many cases, the site will be displayed without SSL/TLS. This is effective against a user who isn’t paying attention; but luckily, there are defenses for this in many modern browsers. The most effective is a new protocol called HSTS. When a site enables HSTS, it tells the user’s browser to always force SSL/TLS the next time the user loads the site, and not to let them override it (assuming they are using a modern browser). For instance, if you tried to reload the page as http (first of all, it should redirect back to https), if you succeed in connecting as http, your browser will not let you load the page – it will give you a warning that you cannot override. Even if the site does not have HSTS enabled, the browser should warn the user if they are trying to log into a website without SSL/TLS.
![]()
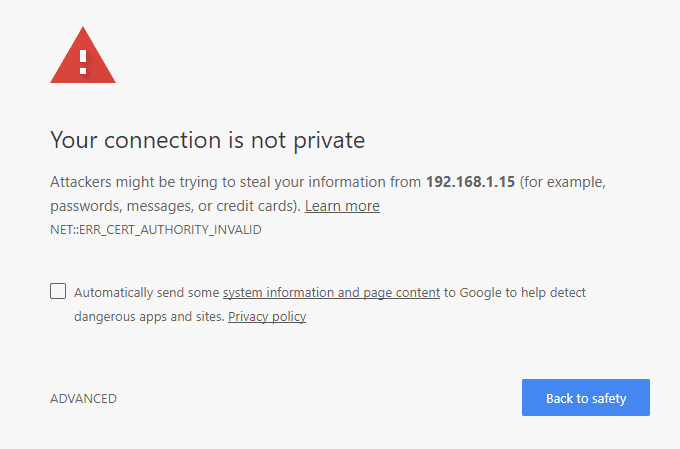
If the attacker wants to run a more sophisticated attack, they can run an SSL intercept proxy such as Burp Suite. (This is the method that I used in my investigation of the Bose connect app.) In this attack, the attacker tries to pose as the browser’s destination again; but this time they load the page over SSL/TLS and re-broadcast the page in SSL/TLS to the legitimate server. This is much harder for the attacker, as they must somehow install a certificate authority on the victim’s computer. As browsers load a website with SSL/TLS, they check the “SSL Certificate”. This is like a digital notary. Your computer keeps a list of trusted authorities whose job it is to verify that a website is who they claim to be. When a trusted certificate authority validates a website, they give them a certificate that is like a digital version of a notary’s stamp stating that the website is who it claims to be. It is impossible to duplicate this certificate unless you have the private key (which is similar to a password). Assuming that the attacker is unable to compromise the private key (which is usually very hard), they must make up a new certificate. The problem is that they are not a trusted authority – they have to convince the computer that they are, otherwise it will display an error like the screenshot below. If the attacker had physical access to the machine, they could do this in about 30 seconds – 1 minute; or it could be accomplished by somehow tricking the user to run malware. (Although, if the user is running malware or letting an attacker gain physical access for 30 seconds – 1 minute, they probably have much bigger problems.)
The last method that I will go over in this article is probably the hardest: gathering the packets and brute forcing them later. In this method, the attacker allows the traffic that is encrypted with SSL/TLS to flow as it normally would, but save a copy of all of the traffic. They would later attempt to brute force the pre-shared key (PSK – this is basically a password) that the majority of the traffic was encrypted with. The problem (for the cracker) is that a person did not come up with this PSK, a computer did. That means that the weaknesses that a password often has when a person up with it (short, common phrases, re-used passwords, etc) does not exist in this “password”, so the attacker can’t take shortcuts, and will need to try every possible combination until they find the key. Even on the most powerful computers (at least until quantum computers become more stable), this can take hundreds of years; so this method is very impractical and almost never used.
All of that sounds scary… wouldn’t a VPN help?
A VPN might offer a little protection against local crackers; but the reality is that you are at the mercy of the VPN provider. A VPN itself is basically a MitM. VPN providers don’t always keep their word. In addition, most consumer VPN providers have you install the VPN by running their software. This software could install a rogue trusted certificate authority on your computer, and direct all of your traffic to an attacker’s computer. It might even be done without the provider knowing about it. It also simply changes where your attack surface is located. An attacker could target users on a VPN service as they exit the VPN provider, or they may be able to get around the (software based) controls that VPN providers use to isolate their clients from each other. At that point, you might almost be better with an attacker located at the coffee shop you are visiting (there is probably a better chance that they are less experienced than an attacker targeting a VPN provider, and there is a much better chance of them getting caught). Not to mention that many corporate networks (including large chain businesses that provide public WiFi) will probably block VPN connections; making it hard for you to use your VPN consistently.
What’s the alternative?
A better alternative is learning about safe computing practices. Start by training yourself to verify that you are always visiting a site that shows the “s” at the end of “https”. Any website that doesn’t use SSL/TLS probably doesn’t deserve your business anyway. (This is the 21st century, and with free certificate SSL/TLS encryption available through letsencrypt and Cloudflare, there really isn’t any excuse for not protecting a site with SSL/TLS.) You can also use the browser extension HTTPS Everywhere to help you remember. The next step is to start using two factor authentication (2fa) everywhere you can. A good page to help find instructions on enabling 2fa for your favorite sites is https://twofactorauth.org/. Once you are done with that, start learning to use a password manager like LastPass, Dashlane, KeePass, or really anything else. When you properly use a password manager, you should be able to use different random passwords on all sites. This way, even if one password is compromised, the rest of your accounts are safe. (It’s also a lot less work to change your password on one site than it is to change it on every site you have ever had an account on.) Once you’ve accomplished these first 3 steps, you are well on your way to being better secured than most people are. If you don’t make yourself an easy target, the chances of your information being compromised is much less.
If you’re still worried about using public WiFi after taking the steps above, try using a hotspot on your phone instead. While it is more expensive (in most cases) than using a VPN provider, it does help get around the negatives of using a privacy VPN. Also, be careful about logging into a sensitive account (such as online banking, investments, etc) from a public area. Even if you are on your hotspot instead of the public WiFi, people can still shoulder surf. Also, be even more careful when you are at work than when you are on a public network. Keep in mind that nothing you do at work can be considered private. The majority of larger corporations can see everything you do on your corporate assets (computers, cell phones, etc), and they may also use monitoring techniques that can allow them to run a SSL intercept proxy without showing a certificate error (since they own your corporate laptop). A good rule of thumb is to never do anything on your corporate asset that you wouldn’t want your boss and the CEO to know about – because they probably do know.
Conclusion
Ditch the tinfoil hat. If you’ve managed to read to the end, you now know techniques that are much more useful than using a privacy VPN. There are exploitation techniques that were not discussed here; but these are the most common, and they are what I consider the most relevant to the discussion of VPNs. I see no reason to use a privacy VPN, and I regularly use public networks. I operate under the assumption that my traffic is always being intercepted, and I act accordingly.